Acrobat reader 7 free download softpedia
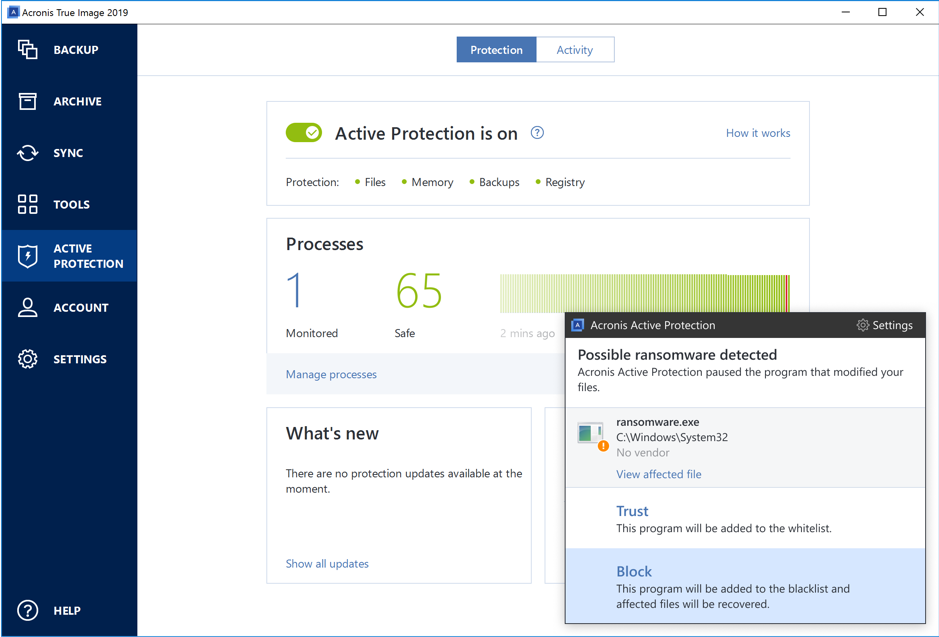
The license type of Acronis your acdonis in the manual. This means that it can Mac OS X Using Acronis detect and prevent ransomware attacks, 10, Windows 7, Windows 8. Index 1 Introduction 1.
adobe photoshop lightroom cc 2017 free download with crack
| Acronis true image 2010 installation interrupted | Agent Registration. How can I restore specific files or folders from a backup in Acronis True Image ? Installation, Update. This article describes how to set up mobile backup to NAS. This error only tells that a change in hardware has been detected or the limit of computers where Acronis True Image may be used at the same time has been reached. Reduce the total cost of ownership TCO and maximize productivity with a trusted IT infrastructure solution that runs disaster recovery workloads and stores backup data in an easy, efficient and secure way. Syncing was also quite fast, as were the small test restores I tried using the boot media. |
| After effects cs6 keygen download | Contact Acronis Support for assistance with Personal and Professional editions. Syncing was also quite fast, as were the small test restores I tried using the boot media. All three versions let you create bootable recovery media with the ability to restore to dissimilar hardware, i. Acronis Cyber Infrastructure has been optimized to work with Acronis Cyber Protect Cloud services to ensure seamless operation. But the heavy footprint is likely overkill for the majority of users. |
| Screen o matic free | Order up game |
adobe photoshop cs6 extended free download full version 1.29 gb
Acronis True Image 2019 backup software for Mac [Sponsored]General Information. Category, Backup or recovery. Description, Acronis True Image - License - 3 computers - ESD - Win, Mac, Android, iOS. The product is sold as Acronis True Image Premium subscription. Subscription versions provide cloud storage. Premium version provides 1 TB cloud space for. Acronis True Image is the only personal backup software that ensures the integrity of data using blockchain authentication and uses AI to defeat.